What is DoS Protection and how to configure it?
DoS attacks (Denial-of-Service attacks) are cyber-attacks that prevent users to access the network resources and services, usually by flooding the target with a large amount of fake traffic. Typical symptoms include:
1) Unusually slow network performance;
2) Unavailability to open a particular web site;
3) Inability to access web sites;
4) Unusual increase in the number of spam emails.
DoS Protection can protect your network against DoS attacks from flooding your network with server requests by monitoring the number of traffic packets. TP-Link routers provide three attack filtering methods in DoS Protection: ICMP-Flood, UDP-Flood, and TCP-Flood.
Follow the steps below, here takes Archer C3150 as demonstration:
1. Login the web interface of TP-Link router by referring to How to log in to the web-based interface of Wi-Fi Routers (new logo)?
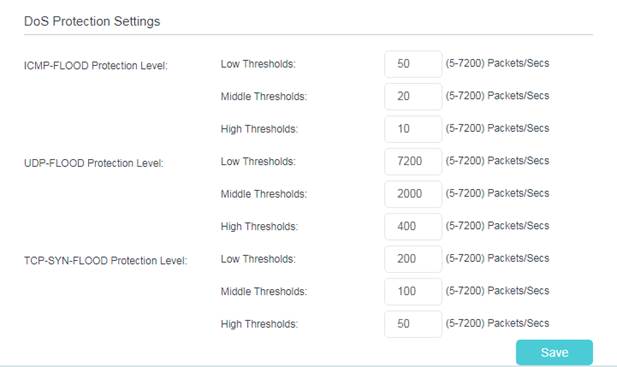
2. Go to Advanced > System Tools > System Parameters to set the threshold value. Click Save.
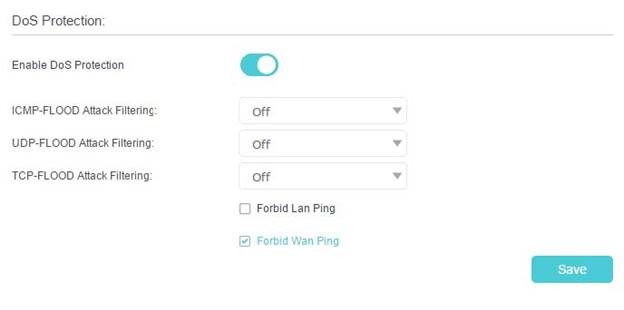
3. Go to Advanced > Security > Settings to enable DoS Protection.
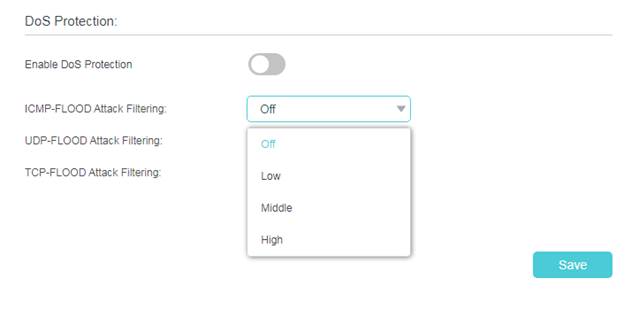
4. Choose the threshold level (Off, Low, Middle or High) for the filtering methods from the drop-down list. Click Save.
1) ICMP-FLOOD Attack Filtering: Enable to prevent the ICMP (Internet Control Message Protocol) flood attack.
2) UDP-FlOOD Attack Filtering: Enable to prevent the UDP (User Datagram Protocol) flood attack.
3) TCP-FLOOD Attack Filtering: Enable to prevent the TCP (Transmission Control Protocol) flood attack.
5. When the number of packets exceeds the preset threshold value, the DoS Protection will be triggered immediately. The vicious host will be displayed in the Blocked DoS Host List.
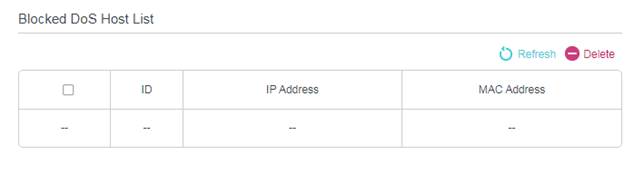
Note: If you find that some client devices cannot have internet access suddenly and are added into Blocked Dos Host List, please check and monitor the network activity of these client devices carefully. You may set threshold value of Dos Protection and the threshold level lower, when you notice that some specific client devices which don’t have any harmful internet behavior are added into Blocked List frequently.
Get to know more details of each function and configuration please go to Download Center to download the manual of your product.
Is this faq useful?
Your feedback helps improve this site.
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.