Our Security Commitment
At TP-Link, security is a core pillar of our product strategy and corporate ethos. Over many years, we have developed and refined a comprehensive security framework designed to anticipate, identify, and address risks swiftly and effectively.
Commitment to Secure Products and Secure Data
Security is embedded into TP-Link’s product development lifecycle. From product planning to release and beyond, our product teams are constantly integrating security measures into product functionality and user experiences. Our investment in security includes an internal penetration testing team, composed of experienced professionals skilled in IoT and embedded systems security, which conducts continuous threat modeling and real-world simulation attacks. We also work with accredited third-party security labs to scrutinize our products and help identify, prioritize, and promptly address potential vulnerabilities before they affect our customers. We act promptly and appropriately when our security teams or outside researchers identify issues, including by designing and issuing security patches.
To ensure our code remains secure throughout the development cycle and cannot be compromised by malicious code or vulnerabilities, TP-Link uses a continuous, automated process for building, testing, and deploying software. Our continuous integration/continuous delivery (CI/CD) pipeline prevents vulnerabilities and backdoors by ensuring that only validated, authorized code progresses through each stage.
Our security commitment equally focuses on protecting user data. We store user data on secure cloud infrastructure protected with industry-recognized security protocols. A U.S.-based information security team oversees core data security functions across TP-Link, and a U.S.-based cloud operations team monitors the security and integrity of U.S. customer data on the cloud.
Data-Driven Evidence of Our Security Posture
TP-Link is committed to being an industry leader in security, and we can demonstrate our commitment through our track record of concrete actions and measurable results. A comparison of publicly available data places TP-Link’s security record on par with or ahead of other major industry players in terms of security outcomes for the common vulnerability scoring system (CVSS), common vulnerabilities and exposures (CVEs), and known exploited vulnerabilities (KEVs).
CVSS Score
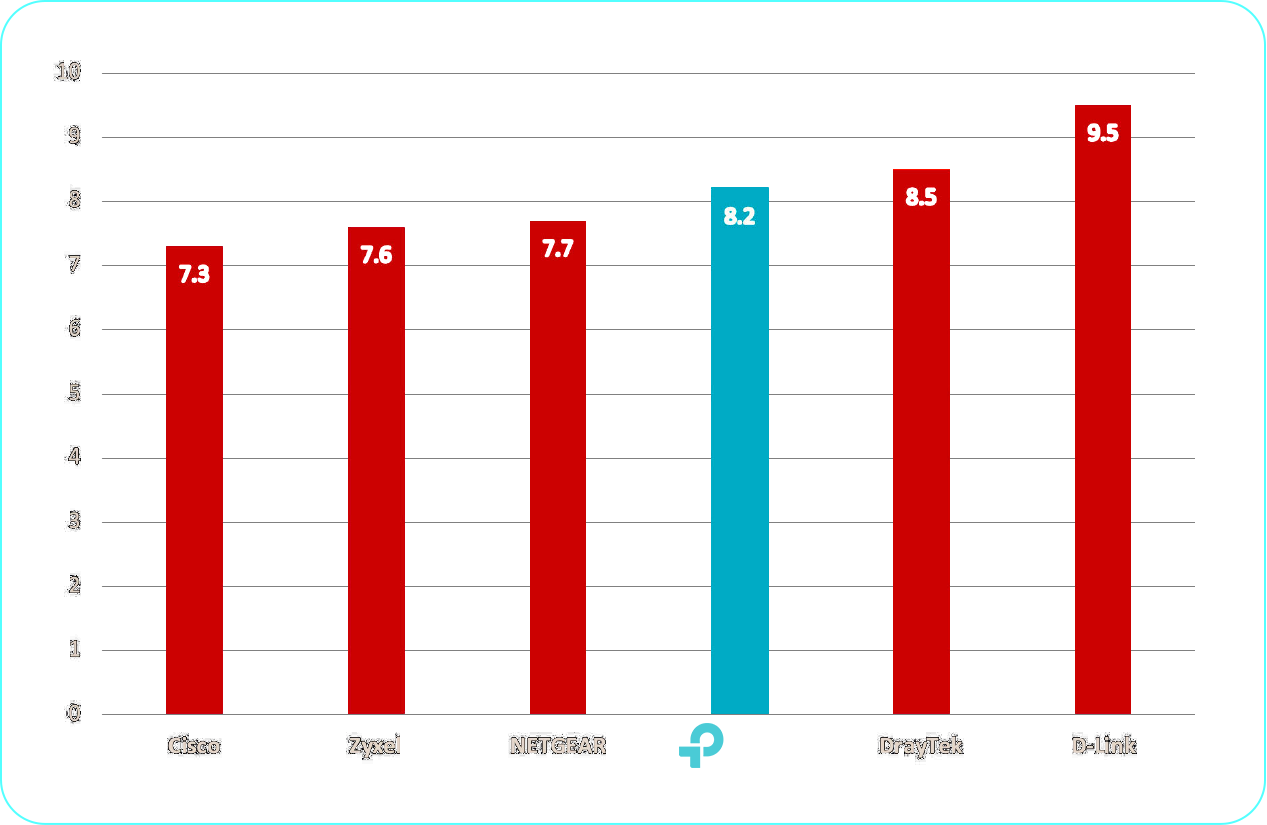
TP-Link’s average weighted CVSS score—an industry-standard metric for vulnerability severity—is in line with that of other leading manufacturers, per 2024 data from individual vendor pages on CVEdetails.com. 1 The average weighted scores for TP-Link and other leading manufacturers are listed in Figure 1, below:
Figure 1: Average Weighted CVSS Score (2024)
CVE Posture
CVEs are standardized identifiers for publicly reported cybersecurity vulnerabilities. TP-Link's vulnerability profile places them in the low-to-middle range among industry peers when assessed by both CVE count and severity.
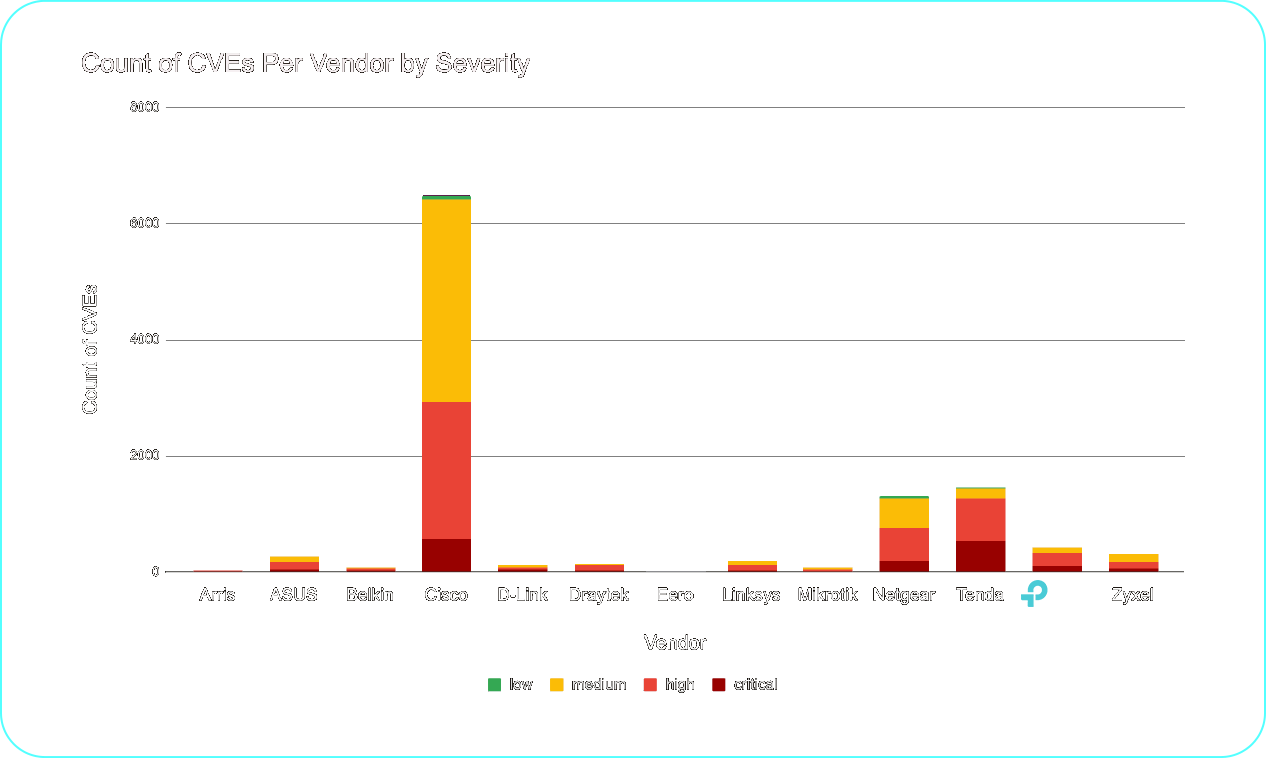
As shown in Figure 2, TP-Link ranks alongside ASUS, Zyxel, and other companies in a middle range of vendors.
TP-Link's severity distribution is evenly balanced across Medium, High, and Critical categories, consistent with most other vendors.
Figure 2: Count of CVEs per vendor, by severity (current as of October 31, 2025)
TP-Link aims to patch vulnerabilities within 90 days of validating them. TP-Link also issues patches for End-of-Life devices in severe cases, a practice not consistently followed by competitors.
KEV Posture
TP-Link's KEV-listed vulnerability count is also mid-range, with some competitors showing dramatically higher counts, and TP-Link has patched all such vulnerabilities, except for one that TP-Link disputes and assesses as improperly listed.
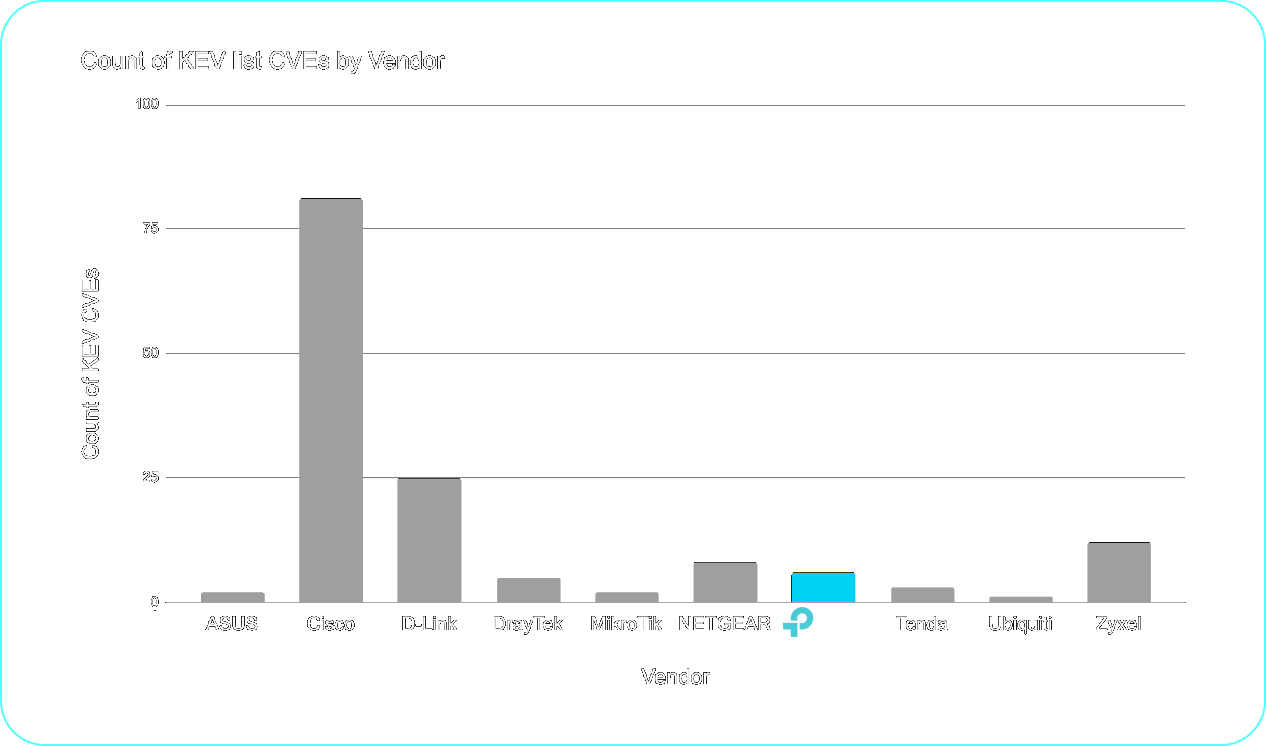
As shown in Figure 3, TP-Link's KEV count is in line with several competitors, but some industry outliers have notably higher counts. For example, Zyxel has approximately twice TP-Link's KEV count, and D-Link has approximately twice again as many.
Figure 3: CISA KEV inclusions by vendor (current as of October 31, 2025)
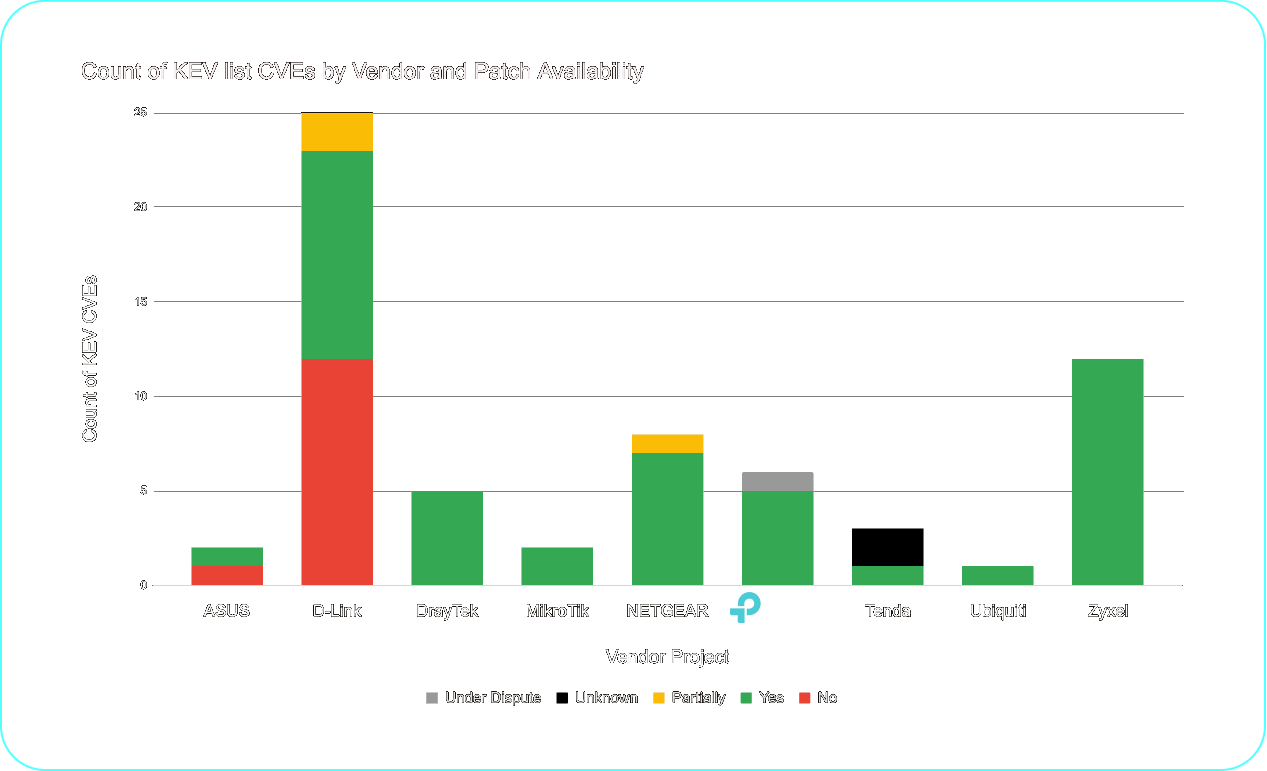
As shown in Figure 4, TP-Link has provided patches for all KEV-listed vulnerabilities (except for one where TP-Link is disputing the validity). This practice is not uniform across the industry, and in particular some suppliers do not issue patches for KEVs associated with end-of-life devices.
Figure 4: Count of KEV CVEs by vendor and patch availability (current as of October 31, 2025)
Default TP-Link configurations are not vulnerable to KEV-listed exploits from the internet at large. For all KEV-listed vulnerabilities associated with TP-Link products, users would only be vulnerable if they were to manually change TP-Link security settings from their defaults. By default, the features associated with these vulnerabilities are either completely disabled or restricted to the local home network only, blocking internet-based attacks. For remote exploitation, users must actively enable remote management features and expose the management interface to the internet. TP-Link explicitly warns users when they attempt to make these configuration changes.
The vast majority of users have not made the deliberate decision to expose their management interfaces to the internet and are therefore not at risk from these KEV-listed vulnerabilities.
Commitment to Secure by Design and Industry Standards
TP-Link strongly supports government-led cybersecurity initiatives and the development of industry standards. We participate in the “Secure by Design” pledge sponsored by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and support the EU’s proposed Cyber Resilience Act (CRA). Since 2022, more than 200 TP-Link products have received security certifications recognized by nations including Finland, Germany, and South Korea. TP-Link strongly supports the development of similar product security standards in the United States and believes that such standards will raise the security baseline for everyone.
Commitment to Transparency
To safeguard the integrity and authenticity of software and firmware components, TP-Link employs industry-accepted mechanisms such as code signing, binary signing, and encryption. These measures ensure that each version of software can be verified as genuine and validate that the software has not been altered or tampered with. These safeguards are critical in preventing attackers from inserting malicious code or backdoors into products in the field.
To enable third-party auditing, faster update times, and clearer insight into our product inputs, TP-Link creates a Software Bill of Materials (SBOM) for every product. SBOMs are comprehensive inventories of a product’s software components and their origins, created for all product release versions in industry-standard formats, inclusive of build-time provenance data. SBOMs create an auditable record that enables third-party validation of every component in a TP-Link product, making it possible to quickly identify and respond to code vulnerabilities. This process is integrated directly into the release workflow to ensure accuracy and traceability at every stage of development and manufacturing.
In addition, we offer prompt firmware and software updates that we link to identified vulnerabilities on the cve.org website, and publish detailed security advisories when appropriate. We also publish and maintain clear end-of-life policies, ensuring customers understand how long their old devices will continue to receive critical updates, and how customers can help ensure device security.
Because TP-Link maintains full visibility and control over its design, development, and production pipeline, SBOM generation and verification are embedded as standard practice rather than regulatory requirements. This voluntary commitment enables complete transparency into software components and their origins, resulting in more secure, reliable products with fewer vulnerabilities and faster security response times.
Engagement with the Security Community
TP-Link actively participates in global security initiatives and in the cybersecurity community. We are a registered CVE Numbering Authority, which means we take direct responsibility for identifying and publicizing cybersecurity vulnerabilities that could potentially affect our products. We engage with third-party partners on activities including security testing of our products, bug bounty programs run on a prominent industry platform, and hacking competitions such as the Zero Day Initiative’s PWN2OWN. TP-Link is an active participant in global security initiatives and has a proactive vulnerability disclosure program. Independent researchers and the security community can report potential issues to us at security@tp-link.com.
Continuous Improvement and Accountability
We back up our words with actions. Our (CI/CD) pipeline allows us to catch issues earlier, and findings from ongoing penetration testing directly inform our product roadmaps. We measure success by the speed at which we respond to vulnerabilities, how effectively we reduce their overall volume, and the trust feedback we receive from customers. TP-Link actively monitors cybersecurity developments globally and stands ready to address any vulnerabilities exploited by advanced persistent threat actors that it becomes aware of.
In short, TP-Link strives to be a leader in IoT and networking security, while acknowledging that security is never final and always evolving. By working with industry experts, embracing government guidance and standards, and maintaining an unwavering focus on improvement, we ensure that our customers can trust our devices, today and in the future.
1 Example CVEdetails for TP-Link Systems: https://www.cvedetails.com/cvss-score-charts.php?fromform=1&vendor_id=11936&product_id=&startdate=2024-01-01&enddate=2024-12-02.