Шаблон исходного кода для внешнего веб-портала (для контроллера версии 4.1.5 и выше)
Данная статья относится к контроллеру версии 4.1.5 и выше.
Для версии 3.1.4 и выше обратитесь к этой статье: https://www.tp-link.com/support/faq/2390/
Для версии 3.0.5 и ниже обратитесь к этой статье: https://www.tp-link.com/support/faq/916/
Данный документ перечисляет требования к серверу внешнего веб-портала. В контроллере Omada внешний веб-портал может быть использован только при типе аутентификации External Radius Server.
Изображение ниже демонстрирует общение между беспроводным клиентом, EAP, контроллером Omada, внешним веб-порталом и RADIUS-сервером. Оно поможет Вам лучше понять требования при установке сервера внешнего веб-портала.
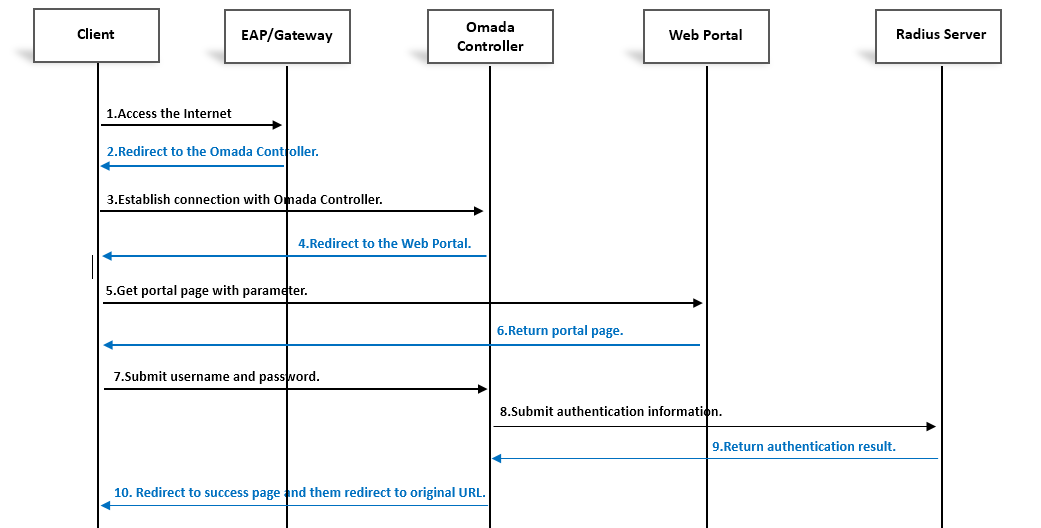
- Когда проводной или беспроводной клиент подключается к точке доступа и пытается выйти в интернет, EAP или шлюз перенаправляет HTTP-запрос клиента на контроллер Omada. (Шаг 1 и Шаг 2).
- Контроллер Omada затем перенаправляет запрос клиента на страницу внешнего портала, отвечая кодом состояния 302. (Шаг 3 и Шаг 4).
- Клиент отправляет запрос HTTP/HTTPS GET внешнему веб-порталу с параметром “?target=target_controller_ip&targetPort=target_controller_port&clientMac=client_mac&clientIp=client_ip&raidusServerIp=radius_server_ip&apMac=ap_mac&gatewayMac=gateway_mac&scheme=scheme&ssidName==ssid_name&radioId=radio_id(0 для диапазона 2.4G, 1 для диапазона 5G)&vid=vid&originUrl=redirecturl(если вы не задали адрес URL для перенаправления после прохождения аутентификации на портале, URL по умолчанию будет зависеть от беспроводных клиентов)
- Внешний веб-портал должен быть способен получить значения параметров clientMac, clientIp, apMac, gatewayMac, ssidName, radioId, vid, scheme, originUrl. Затем сервер внешнего веб-портала должен перенаправить клиента на контроллер с информацией о username, password, clientMac, clientIp, apMac, gatewayMac, ssidName, scheme, vid, radioId, originUrl (Шаг 6).
- Клиент отправляет пакеты HTTP/HTTPS POST на (http) https://target_controller_ip:targetport/portal/radius/auth (или radius/browserauth) в формате JSON (или формы HTML) в теле сообщения HTTP после подтверждения. targetport по умолчанию – 8843 (Шаг 7). Чтобы понять различие между radius/auth и radius/browserauth обратитесь к разделу Демо и api данной статьи.
Примечание: при использовании контроллера версии 5.0 поле Access-Control-Allow-Origin:URL должно быть предоставлено в HTTP header, чтобы улучшить защиту при Cross-Origin Resource Sharing (CORS). Например, если доменное имя внешнего веб-портала – www.tplinkportal.com, нужно добавить Access-Control-Allow-Origin:https://www.tplinkportal.com. Пожалуйста, скачайте демонстрационный файл в конце этой статьи.
- Контроллер Omada обменивается данными с RADIUS-сервером, чтобы подтвердить username и password. (Шаг 8 и Шаг 9)
- Если аутентификация пройдена, например, от RADIUS-сервера получен ответ Access-Accept, контроллер Omada перенаправит клиента на встроенную страницу успешной авторизации или предустановленную веб-страницу, в соответствии с настройками клиентов. (Шаг 10)
Демо и api
Для версий с 4.1.5 по 5.1.0 мы предоставляем api: https://target_controller_ip:targetport/portal/radius/auth в формате JSON
Шаблон html, предоставленный ниже – демонстрация того, как вы можете настроить работу внешнего веб-портала с контроллером Omada с использованием формата JSON:
External Web Server Demo (JSON)
При использовании HTTPS на стороне веб-портала и HTTP на стороне контроллера Omada, AJAX может вызывать проблемы с кросс-доменным доступом (CORS) и быть перехваченным браузером, поэтому мы предоставляем api для формы HTML, начиная с контроллера версии 5.3.1: target_controller_ip:targetport/portal/radius/browserauth
Шаблон html ниже – это демонстрация использования формы HTML
External Web Server Demo (HTML form)
Примечание:
- Если ваш контроллер версии 4.1.5 и выше обновлен с контроллера 3.x.x, обратите внимание, что имена некоторых параметров изменены.
|
Имя(V3.x) |
Имя(V4.x) |
Тип |
Примечание |
|
clientMac |
clientMac |
string |
MAC-адрес клиента |
|
clientIp |
clientIp |
string |
IP-адрес клиента |
|
ap |
apMac |
string |
MAC-адрес точки доступа (только для ap) |
|
gatewayMac |
string |
MAC-адрес шлюза (только для проводного соединения) |
|
|
vid |
integer |
vid (только для проводного соединения) |
|
|
ssid |
ssidName |
string |
|
|
radioId |
radioId |
integer |
0: 2.4GHz, 1: 5GHz(только для ap) |
|
/ |
authType |
integer |
Тип аутентификации 2: External RADIUS; 8: Hotspot RADIUS |
|
redirectUrl |
originUrl |
string |
URL для перенаправления |
|
username |
username |
string |
Имя пользователя для аутентификации |
|
password |
password |
string |
Пароль для аутентификации |
Обратите внимание, что apMac и gatewayMac не могут существовать одновременно в одном запросе. В случае подключения клиентов по кабелю, оставьте apMac пустым.
- В шаге 7, если в форме содержаться символы не кодировки ASCII (например, имя SSID на китайском или другом языке), следует использовать кодировку UTF-8 при отправке HTTP/HTTPS POST на контроллер.
- Если вы выбрали AJAX, обратите внимание на поле “Access-Control-Allow-Origin:URL” для контроллера версии 5.0 или выше.
- Рекомендуется использовать демо формы HTML и radius/browserauth api
Приложение: API для auth и browserauth
portal/radius/auth (начиная с Omada Controller 4.1.5)
Основная информация
Путь: /portal/radius/auth
Метод: POST
Параметры запроса
Headers
|
Параметры |
Значения |
Требуется |
|
Content-Type |
application/json |
Да |
Query
|
Параметры |
Требуется |
Описание |
|
key |
Да |
Ключ AES зашифрованный публичным ключом RSA, RSA/ECB/PKCS1Padding. Первые 16 байтов – ключ, последние 16 байтов – IV. Этот 32-байтный ключ должен быть в кодировке URLBase64. |
Body
|
Параметры |
Тип |
Требуется |
Описание |
|
clientMac |
string |
Да |
MAC-адрес клиента |
|
clientIP |
String |
IP-адрес клиента |
|
|
apMac |
string |
Да |
MAC-адрес точки доступа |
|
gatewayMac |
string |
Да |
MAC-адрес шлюза |
|
ssidName |
string |
Да |
Имя SSID |
|
vid |
integer |
Да |
VLAN ID |
|
radioId |
integer |
Да |
0: 2.4GHz 1: 5GHz |
|
authType |
integer |
Да |
Тип аутентификации 2: External RADIUS 8: Hotspot RADIUS |
|
originUrl |
string |
URL для перенаправления |
|
|
username |
string |
Да |
Имя пользователя для аутентификации |
|
password |
string |
Да |
Пароль для аутентификации |
Параметры ответа
|
Параметры |
Тип |
Требуется |
Описание |
|
errorCode |
integer |
Да |
Код ошибки |
portal/radius/browserauth (начиная с Omada Controller 5.3.1)
Основная информация
Путь: /portal/radius/browserauth
Метод: POST
Параметры запроса
Headers
|
Параметры |
Значение |
Требуется |
|
Content-Type |
application/x-www-form-urlencoded |
Да |
Параметры пути
|
Параметры |
Тип |
Требуется |
Описание |
|
clientMac |
string |
Да |
MAC-адрес клиента |
|
clientIP |
String |
IP-адрес клиента |
|
|
apMac |
string |
Да |
MAC-адрес точки доступа |
|
gatewayMac |
string |
Да |
MAC-адрес шлюза |
|
ssidName |
string |
Да |
Имя SSID |
|
vid |
integer |
Да |
VLAN ID |
|
radioId |
integer |
Да |
0: 2.4GHz 1: 5GHz |
|
authType |
integer |
Да |
Тип аутентификации 2: External RADIUS 8: Hotspot RADIUS |
|
originUrl |
string |
URL для перенаправления |
|
|
username |
string |
Да |
Имя пользователя для аутентификации |
|
password |
string |
Да |
Пароль для аутентификации |
Параметры ответа
|
Параметры |
Тип |
Требуется |
Описание |
|
errorCode |
integer |
Да |
Код ошибки |
Полезен ли этот FAQ?
Ваши отзывы помогают улучшить этот сайт.
From United States?
Получайте информацию о продуктах, событиях и услугах для вашего региона.
1.0_normal_20211214093252a.png)

