FAQ: Basic Wireless Concepts
CHAPTERS
1. What Are the Main Differences Among 802.11a/b/g/n/ac/ac wave2 Standards?
2. What Kind of Interference Sources Are There in WLAN?
3. What Is the Difference Between WLAN and Wi-Fi and How Do They Relate to Each Other?
5. What Is Beamforming Technology?
6. What Are TDMA and MAXtream?
7. What is the Difference among HT20, HT40 and HT80?
9. What Is the Working Principle of 802.11n Short GI?
10. What Does WLAN Rate Refer to?
11. What Are the Physical Rate, Theoretical Rate, and Actual Rate in the 802.11 Standard?
13. What is the Difference Between IEEE 802.11e and WMM?
14. What Are the Common Wireless Encryption Methods? And What Are the Differences Between Them?
15. What Are Beacon Interval, RTS Threshold and DTIM Period?
16. What Is MCS in 802.11n and 802.11ac?
17. Does the Station Listen to Beacon Frames and Send/Receive Data Frames over One Channel?
18. What Is Band Steering Used for?
19. What Are the Commonly-used Units in Wireless Signal Transmission?
|
|
This guide applies to: Omada/Pharos Series Products |
1What Are the Main Differences Among 802.11a/b/g/n/ac/ac wave2 Standards?
The standards are summarized in Table1 and vary in frequency band and rate.
Table 1Differences among 802.11a/b/g/n/ac/ac wave2
|
Protocol |
Frequency Band |
Compatibility |
Physical Rate |
|
802.11b |
2.4GHz |
N/A |
11Mbps |
|
802.11g |
802.11b |
54Mbps |
|
|
802.11n |
2.4GHz, 5GHz |
802.11a/b/g |
600Mbps |
|
802.11a |
5GHz |
N/A |
54Mbps |
|
802.11ac |
802.11a/n |
1.3Gbps |
|
|
802.11ac wave2 |
802.11a/n/ac |
6.9Gbps |
2What Kind of Interference Sources Are There in WLAN?
There are many kinds of wireless interference encountered in daily life. When deploying a wireless network, these interferences may influence the network capability. The interference sources and the methods to reduce their effects are explained below.
In a large wireless network such as a campus wireless network, there are often multiple wireless devices. If these wireless devices work in the same channel and can see each other, it may result in the co-channel interference according to CSMA/CA. If these wireless devices work in the adjacent channels and can see each other, it may result in the adjacent channel interference. Therefore, when deploying a large wireless network, it is recommended to use non-overlapping channels such as 1, 6, 11 channels in 2.4G band.
When deploying wireless devices in the home, there are certain sources of interference that should be considered. Some devices such as microwave ovens and cordless phones work in 2.4GHz or 5GHz frequency bands as well as the devices in WLAN, and the signal produced by these devices may cause the external interference.
Microwave ovens, as well as most WLAN devices, mainly operate within 2.4GHz-2.5GHz frequency bands. This means that microwave ovens can have a significant impact on the performance of WLAN devices. Cordless phones also work in the 2.4GHz frequency band. If cordless phones are too close to the WLAN devices, the call quality and rate of wireless communication will both be affected. IP camera and Bluetooth devices can influence the throughput of the wireless network as well.
Taking these considerations into account, it is better to keep WLAN devices away from potential sources of interference. Also, try to avoid using the devices mentioned above and WLAN devices at the same time.
3What Is the Difference Between WLAN and Wi-Fi and How Do They Relate to Each Other?
WLAN is short for wireless local area network. It is a compliment to LAN (local area network). WLAN links several wireless devices by using the RF (Radio Frequency) technology and is mostly based on IEEE 802.11 standards. In addition, WLAN also use other standards such as HIPERLAN2 in some areas.
Wi-Fi is a trademark owned by Wi-Fi Alliance. It represents a technology of WLAN complying with IEEE 802.11 standards. The products from different manufacturers using this trademark have a good interoperability with each other.
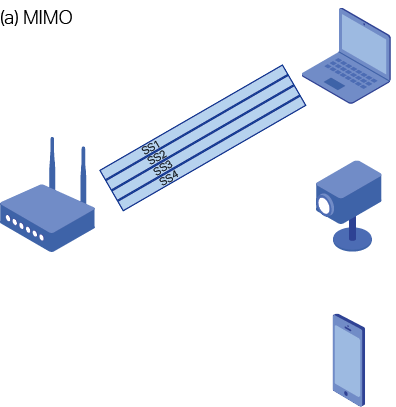
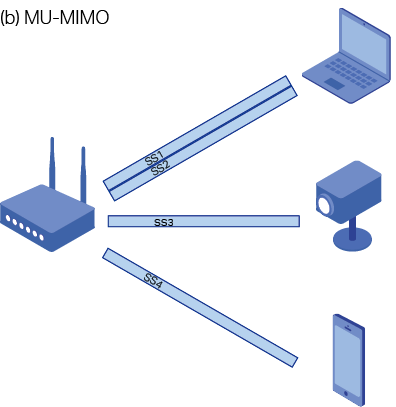
■MIMO (Multiple-Input Multiple-Output) is a technique that was first introduced with the 802.11n standard to multiply the capacity of radio links. The MIMO system consists of multiple transmitting antennas and multiple receiving antennas. All the transmitting antennas forward data at the same time, which generates multiple spatial streams, The receiving antennas can pick out the signal from different spatial paths and reconstruct the original signal. MIMO can improve the throughput of the wireless network. 802.11n supports four transmitting antennas and four receiving antennas at most, and can achieve transfer rates of up to 600Mbps.
■MU-MIMO (Multi-User Multiple-Input Multiple-Output) is a technological improvement on MIMO that is used in the 802.11ac standard. In MIMO, the transmitter can only communicate with one user at a time. However, in MU-MIMO system, the transmitter can transmit data to multiple users at the same time, making better use of the available space resources.
Figure 1 shows the difference between MIMO and MU-MIMO.
Figure 1 Difference between MIMO and MU-MIMO
5What Is Beamforming Technology?
Beamforming is the combination of antenna technology and signal processing technology used in the MIMO system. It processes the signals sent by multiple antennas to generate a directional signal. As for receivers, beamforming produces a directional radiation pattern to adapt the signal from the transmitter. Beamforming helps to improve SNR (signal-to-noise ratio) and the signal coverage.
■TDMA (time division multiple access) is a digital transmission technology, and it is one part of Multiple Access technologies. TDMA divides time into periodic and non-overlapping frames, then divides each frame into several time slots. Each user in the network is allocated a fixed time slot, and only can transmit or receive data in its own slot. TDMA allows multiple users to share the same frequency channel to increase the utilization of frequency band. Another advantage of TDMA is that it reduces interference among users.
■MAXtream is a TP-Link proprietary protocol based on TDMA. It can deal with the hidden node challenge and is much better than RTS/CTS function. It works in the same way as TDMA. Users transmit data in their own slots, which avoids the conflict caused by hidden nodes.
7What is the Difference among HT20, HT40 and HT80?
HT20 (High Throughput 20) means that the wireless devices working with 20MHz channel. Likewise, HT40 and HT80 use 40MHz and 80MHz channel respectively. By default, wireless devices use 20MHz channel. To improve the speed, HT40 broadens the bandwidth by binding two continuous 20MHz channels or discontinuous 20MHz channels. HT80 binds four 20MHz channels to get a higher speed than HT40. 802.11n and 802.11ac both can supply 20MHz and 40MHz channels to be used in WLAN. In addition, 802.11ac extends the technology to HT80.
802.11a/b/g standards don’t support HT40 and HT80, so HT40 and HT80 can’t be used in mixed mode such as 802.11b/g/n mixed mode.
Because of the channel partition in the 2.4GHz frequency band, only one non-overlapping 40MHz channel can be set in the 2.4GHz band. Therefore, HT40 can be affected easily in the 2.4GHz band. HT20 is better than HT40 in the 2.4GHz frequency band. There are twenty four non-overlapping 20MHz channels. Twelve 40MHz channels or six 80MHz channels can be set in the 5GHz band. For reasonable channel layout, it is recommended to use four to six channels, so HT40 and HT80 are suitable for the 5GHz band.
8What Is the Difference Between ESS and BSS, and Between SSID, BSSID and ESSID? How Do They Relate to One Another?
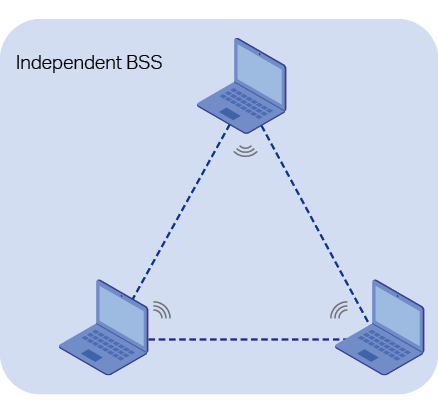
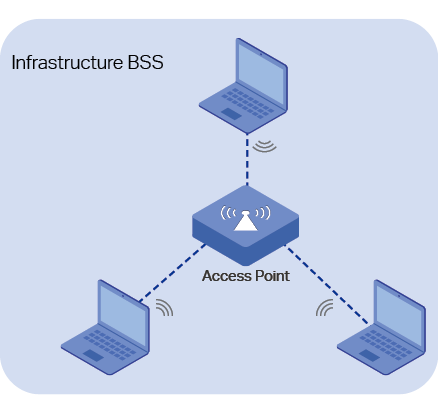
■BSS (basic service set) provides a basic building-block of an 802.11 wireless network. It is a group of terminals working in the same basic service area. There are two types of BSS: Independent BSS (IBSS) and Infrastructure BSS. IBSS is also known as ad hoc BSS. Terminals in IBSS communicate with each other directly. Different from IBSS, there must be an AP in Infrastructure BSS and it is necessary for the terminals in infrastructure BSS to communicate with each other through the AP. Figure 2 shows the structures of Independent BSS and Infrastructure BSS.
Figure 2 The Structures of Independent BSS and Infrastructure BSS
■An ESS (extended service set) consists of more than one BSS by connecting APs in different BSS. Terminals in the same ESS can communicate with each other. Figure 3 shows the structure of ESS.
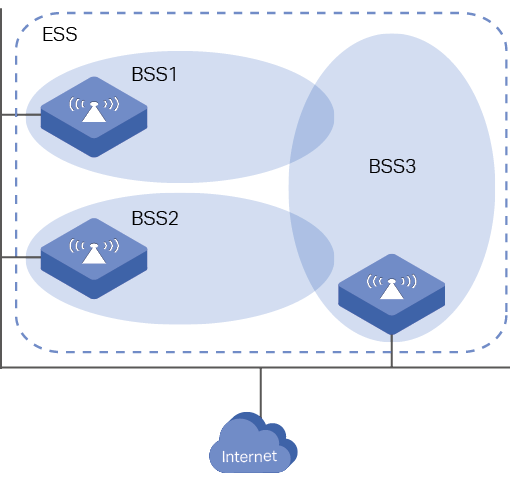
The coverage of BSS is limited by the distance between terminals or the coverage of the AP, so BSS can only serve a small office or home. ESS provides a much larger coverage than BSS.
■SSID identifies different wireless networks. It can be specified manually and it is commonly referred to as Wi-Fi name or network name..
■BSSID is used to identify a BSS in an ESS. Each BSS has its own BSSID. The BSSID is decided by the manufacturers, and it is usually related to the device’s MAC address. The BSSID can’t be modified manually.
■ESSID is used in ESS network. The wireless networks we often talked about nowadays are usually ESS network, and the ESSID is the equivalent of SSID. An ESSID is set using APs. Only terminals that use the same ESSID as the APs can access the network.
9What Is the Working Principle of 802.11n Short GI?
Propagation delays often occurs in data transmission process and influence the capability of the wireless network. It can result from multiple factors, such as multipath effect. GI (Guard Interval) is intended to solve the problem based on delays, and Short GI is used to improve the throughput of the wireless network based on the GI in the environment with small delays.
Data frames will be divided into several symbols when being transmitted. If there are severe propagation delays during the transmission, the latter symbol will interfere with the earlier symbol. To avoid this kind of interference, GI is added at the beginning of every symbol. GI is usually set as 800ns. It can be cut down properly to shorten the interval between two frames when the delays are small. When Short GI is enabled, the guard interval will be set as 400ns and this function will boost the performance about 11%.
When deploying a wireless network in an environment with many obstacles, there will be diffraction, scattering and reflection. The situation above can result in serious multipath time delay. Short GI function will reduce the throughput instead of improving it. Therefore, it is recommended to not use Short GI in a situation where the multipath effect is significant.
10What Does WLAN Rate Refer to?
WLAN (wireless local area network) rate refers to the data transmission rate between two wireless devices. In a wireless network, devices work in half-duplex mode. This means they can send or receive data at the same time. The rate of sending data is called upstream rate, and the rate of receiving data is called downstream rate. Generally, the WLAN rate is the sum of upstream traffic and downstream traffic per unit time. In reality, when we browse the web or download a movie the majority of the traffic is downstream traffic, so in these cases the WLAN rate approximately equals the downstream rate.
11What Are the Physical Rate, Theoretical Rate, and Actual Rate in the 802.11 Standard?
Physical rate is the physical layer rate of a radio interface which continually sends data. For example, the physical rate of 802.11b is 11Mbit/s.
Theoretical rate takes the following factors into account: packet header, checksum bits, link code, PLCP header, transmission delay and ACK frame transmission time. For the 802.11b standard, if we take the 1500-byte UDP data frames as an example, the calculated theoretical rate is 7.1 Mbit/s.
Actual rate, in addition to the factors above, takes into account the number of stations, any obstacles present in the surroundings, and more. These factors will affect the AP performance. The following table shows some typical physical rates and the corresponding actual rates.
Table 2Physical Rate and Actual Rate
|
Protocol |
Physical Rate (Mbit/s) |
Actual Rate (Mbit/s) |
|
802.11b |
11 |
4.7 |
|
802.11g |
54 |
20 |
|
802.11a |
54 |
20 |
|
802.11n |
600 |
410 |
|
802.11ac |
1300 |
510 |
12Why Does the Overall Throughput Decrease When 802.11g, 802.11n and 802.11ac Are Used at the Same Time on the Wireless Network? How Can I Resolve This Problem?
Devices using different wireless protocols have different wireless transmission rates. Among the three protocols, 802.11g supports the lowest rate, and 802.11ac supports the highest rate. When there are several stations respectively using 802.11g, 802.11n and 802.11ac to communicate with an AP, the slower stations take more time to transmit and receive data compared to the faster stations. This gives less time to the faster stations for data transmission. As a result, the overall wireless throughput of the network decreases.
However, under some circumstances, it is inevitable that different protocols are used at the same time. To reduce the impact of mixed usage of different protocols, some APs provide the Airtime Fairness feature.
The working mechanism of Airtime Fairness is different among TP-Link products. EAP320/EAP330 gives equal amounts of transmission time to each station regardless of its physical rate. CAP1750/CAP1200 gives transmission time to the stations according to their physical rates. The faster stations get more time for data transmission and the lower stations get less. In both ways above, the data transmission time for the faster stations is ensured, and the overall wireless throughput increases.
13What is the Difference Between IEEE 802.11e and WMM?
The early IEEE 802.11 standard does not support QoS (Quality of Service), meaning that all applications have equal opportunity to transmit data. That works well for applications such as web browser and email. But for delay-sensitive multimedia applications such as VoIP and video streaming, the traffic quality should be highly guaranteed. To meet this need, IEEE 802.11e was established as an approved amendment to IEEE 802.11 standard. IEEE 802.11e defines a set of MAC layer QoS enhancements for wireless delay-sensitive applications.
WMM (Wi-Fi Multi-Media) is a subset of IEEE 802.11e. It defines four access categories with priority from high to low: voice, video, best effort and background. With WMM properly configured, delay-sensitive data from applications like VoIP, streaming media and video will get a higher priority to be sent, and other less delay-sensitive data will get a lower priority to be sent. WMM optimizes network communication quality for different applications and ensures their stable access to network resources.
All TP-Link business Wi-Fi products support WMM.
The following figure is a WMM configuration page on the EAP Controller. To use this feature, you can simply check the box to enable WMM and keep the EDCA (Enhanced Distributed Channel Access) parameters as default.
Figure 4 WMM Configuration
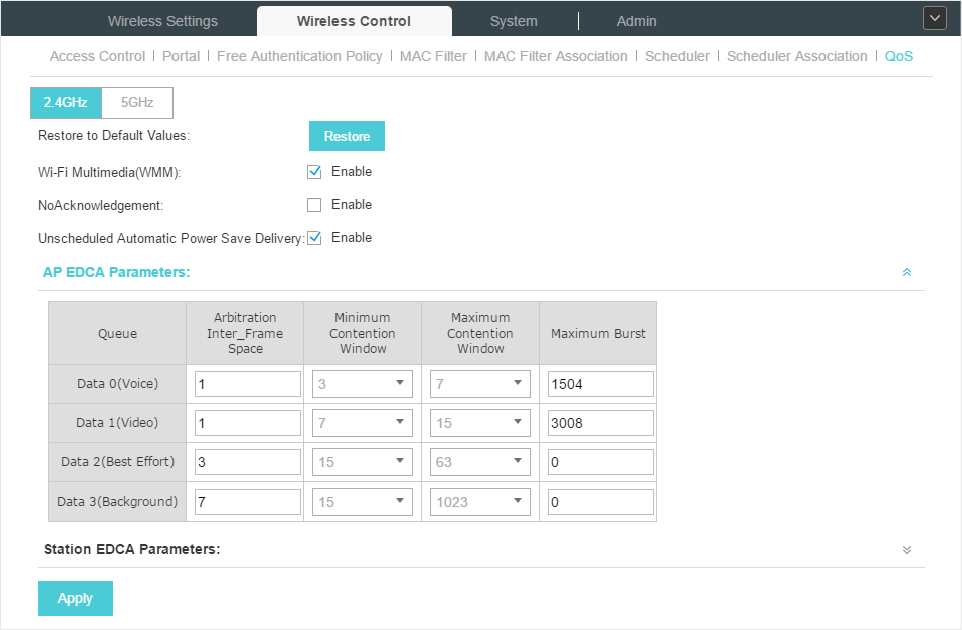
14What Are the Common Wireless Encryption Methods? And What Are the Differences Between Them?
The most widely used wireless encryption methods are WEP, WPA, and WPA2.
WEP (Wired Equivalent Privacy) is a traditional encryption method, which is based on RC4 stream cipher algorithm. The station and the AP share a same WEP key to encrypt and decrypt the data. It has been proved that WEP has security flaws and can easily be cracked, so WEP cannot provide effective protection for wireless networks. If both your stations and AP support another safer encryption method, it is recommended to use the better one.
WPA (Wi-Fi Protected Access) is a safer encryption method, which is based on RC4 algorithm and TKIP encryption. WPA has two versions: WPA-PSK (WPA-Pre-shared Key) and WPA-Enterprise. WPA-PSK uses Pre-shared key to authenticate the users. WPA-Enterprise requires a RADIUS server to authenticate the users via 802.1X and EAP (Extensible Authentication Protocol). WPA2 ensures higher security but also costs more to maintain the network, so it is more suitable for business networks.
WPA2 is an update of WPA. Compared with WPA, WPA2 introduces AES algorithm and CCMP encryption, and also keeps RC4/TKIP as an optional encryption way. Similarly, WPA2 includes WPA2-PSK and WPA2-Enterprise.
The following table briefly displays each encryption method introduced above.
Table 3Encryption Mode
|
Encryption Mode |
Algorithm |
Encryption |
Authentication |
Security Strength |
|
|
WEP |
RC4 |
WEP |
Open System Shared Key |
Low |
|
|
WPA |
WPA-PSK |
RC4 |
TKIP |
WPA-PSK |
Normal |
|
WPA-Enterprise |
802.1X/EAP |
High |
|||
|
WPA2 |
WPA2-PSK |
AES RC4 |
CCMP TKIP |
WPA2-PSK |
High |
|
WPA2-Enterprise |
802.1X/EAP |
Very High |
|||
15What Are Beacon Interval, RTS Threshold and DTIM Period?
In wireless products, there are some advanced wireless parameters to be configured, such as Beacon Interval, RTS Threshold and DTIM Period. For good performance of the wireless network, these advanced parameters should be properly configured. The following sections introduce the three parameters above:
Beacon Interval
Beacon frames are sent periodically by the AP to announce to the stations the presence of a wireless network. Beacon Interval determines the time interval of the beacon frames sent by the AP device.
With a low beacon interval, the AP device will send beacon frames more frequently, which can ensure the constant wireless connection for the fast moving stations. But at the same time, more wireless bandwidth will be consumed.
RTS Threshold
RTS/CTS (Request to Send/Clear to Send) is used to improve the data transmission efficiency of the network with hidden nodes, especially when there are lots of large packets to be transmitted. With RTS/CTS mechanism activated, before sending a data packet, the station will send an RTS packet to the AP to request data transmitting. And then the AP will send CTS packet to inform other stations to delay their data transmitting. In this way, packet collisions can be avoided. However, if the station sends RTS packet every time when it prepares to send a data packet, much bandwidth will be consumed. So only when the size of data packet is larger than the RTS Threshold will the RTS mechanism be activated.
An appropriate RTS Threshold value is important. For a busy network with hidden nodes, a low threshold value will help reduce interference and packet collisions. But for a not-so-busy network, a too low threshold value will cause bandwidth wasting and reduce the data throughput.
DTIM Period
The DTIM (Delivery Traffic Indication Message) is contained in some Beacon frames. It is used to tell the stations that the AP has buffered multicast data to be sent. For a station in Power Save mode, if it receives a beacon frame containing DTIM, it will remain awake, ready to receive the data. DTIM Period indicates how often the beacon frames will contain DTIM. For example, 3 indicates that DTIM will be contained every 3 beacon frames. An excessive DTIM interval may reduce the performance of multicast applications.
16What Is MCS in 802.11n and 802.11ac?
In TP-Link Pharos series products, there is a wireless configuration option named Max TX Rate, and the options may include MCS1, MCS2 and so on in 802.11n and 802.11ac modes.
MCS (Modulation and Coding Scheme) is mainly used to facilitate the maximum wireless rate configuration for 802.11n and 802.11ac.
In 802.11n and 802.11ac, the maximum physical rate is determined by variable factors: modulation mode, coding rate, the number of spacial streams and channel bandwidth. Different combinations of these factors determine different rates. MCS simply uses indexes to represent these combinations.
The following table shows the physical rate each MCS index corresponds to. The MCS indexes are in the table columns, and the variable factors are in the table rows. Each MCS index represents a specific physical rate determined by the specific factor combination, and a higher MCS index indicates a higher physical rate. Under the same conditions, double spacial streams leads to a double rate.
Table 4MCS Index
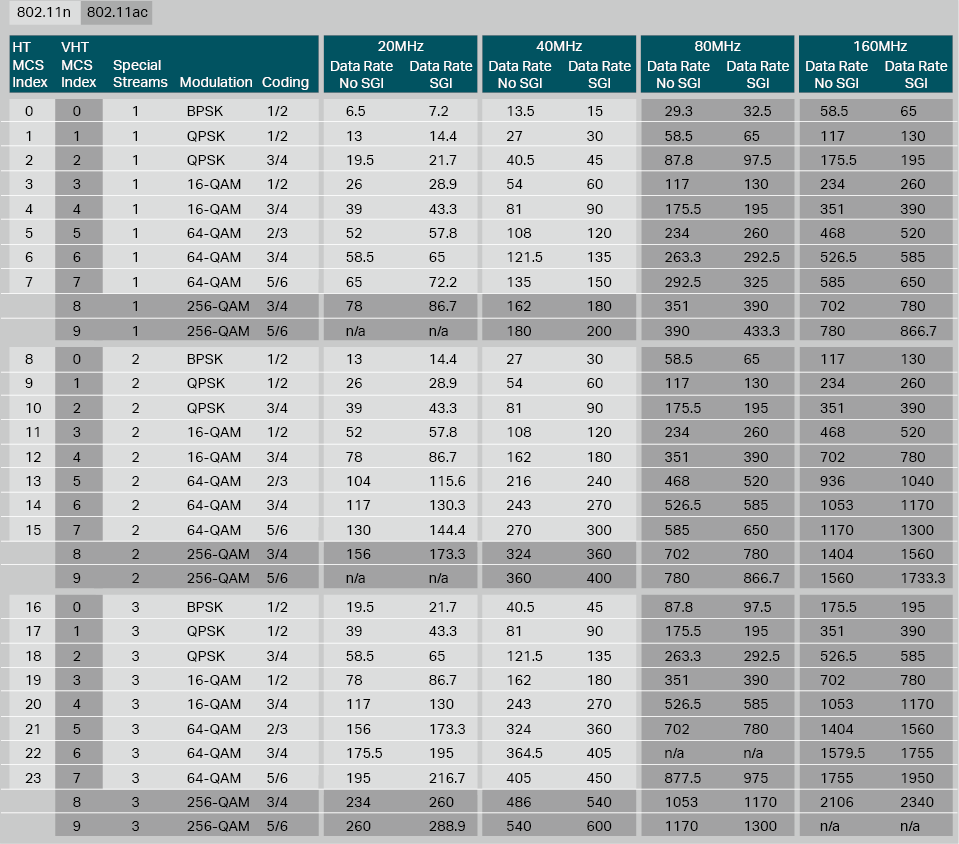
Additionally, 802.11ac supports modulation 256-QAM. This kind of modulation provides a better physical rate, but has higher requirements for the wireless transmission environment. Generally, it is suggested to use 256-QAM only when the stations are close enough to the AP.
17Does the Station Listen to Beacon Frames and Send/Receive Data Frames over One Channel?
The station listens to management frames such as beacon frames over all channels. And when the data transmission channel is determined, the station sends and receives data frames over one specific channel.
Note that the wireless device cannot send or receive the above frames at the same time because of half-duplex communication of the wireless network.
18What Is Band Steering Used for?
Band Steering is an advanced wireless feature in TP-Link dual-band EAP and CAP products.
If a station is capable of communicating on both the 2.4GHz and 5GHz frequency bands, it will typically connect to the 2.4 GHz band. However, if too many stations are connected to an AP on the 2.4 GHz band, the efficiency of communication will be diminished. Band Steering can steer the stations capable of communication on both frequency bands to the 5GHz frequency band. Since the 5GHz band supports a greater number of non-overlapping channels and is less noisy, this feature significantly improves network quality.
|
|
Note: To run the Band Steering function, please create an SSID on both of the 2GHz band and 5GHz band, and make sure the two SSIDs have the same name, security mode and wireless password. |
19What Are the Commonly-used Units in Wireless Signal Transmission?
In wireless signal transmission, specialized units are used for different wireless parameters. These are introduced here.
mW
It is a measurement for transmission power. One mW is a thousandth of a Watt (W). The reason why we use mW instead of W to describe wireless transmission power is that the transmission power of most wireless devices ranges from 1mW to 100mW.
dB
dB (decibel) is a logarithmic unit used to express the ratio of two power values. The calculation formula is dB=10log₁₀ (P1/P2), where P1 and P2 are power values. For example, if the transmit power on the AP is 100mW and the received power on the station is 0.000001mW, the power loss is 100mW minus 0.000001mW. Also we can calculate like this: 10log₁₀ (100/0.000001)=70dB, which represents the change of power more conveniently. This unit is often used to describe SNR (Signal Noise Ratio) and signal loss, such as path loss and cable loss.
dBm
dBm is a unit used to measure an absolute power value. It is the ratio of the power value and 1mW. The calculation formula is dBm=10log₁₀ (P/1mW). For example, 0.00001 mW and 10000mW can also be expressed as -50dBm and 40dBm. As we can see, dBm can express both very large and very small values in a short form. So this unit is often used to describe the Tx power and the Rx power of the wireless devices. In addition, two values in dBm can be calculated directly. Taking SNR (Signal Noise Ratio) as an example, if the received signal power is -85dBm and the background noise is -100dBm, SNR equals -85dBm minus -100dBm, which is 15dB.
dBi
dBi is a unit used to express the gain of an antenna compared with the hypothetical isotropic antenna. For an antenna, a larger dBi value means a stronger capability to force the signal in a specific direction.
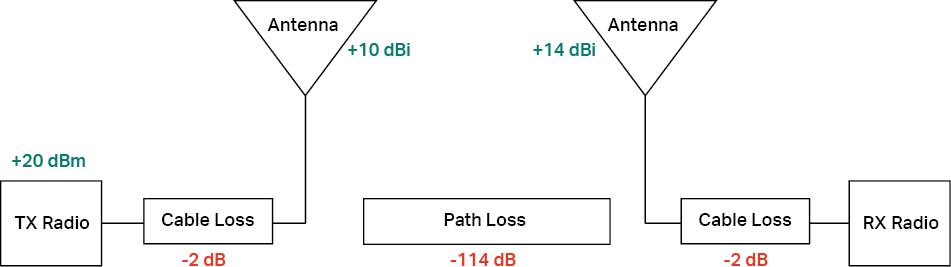
In addition, the values in dB, dBm and dBi can be directly added or subtracted from each other. The following picture shows a signal transmission system. To get the RX radio power, we can directly calculate like this:
Rx power=20dBm-2dB+10dBi-114dB+14dBi-2dB=-74dBm.
Signal Transmission System