Cómo limitar el acceso a un servidor interno mediante una dirección IP específica mediante un router SMB de TP-LINK
Escenario de aplicación
En algunos casos, solo queremos que solo algunas IP externas específicas accedan al servidor interno detrás del router TP-LINK SMB. Esta demanda puede ser satisfecha por el Servidor Virtual con Control de Acceso.
Ahora tomamos el TL-ER6120 v2 como ejemplo. El servidor web está detrás del puerto LAN TL-ER6120 como 192.168.0.2:8080. Y el cliente se encuentra en 14.28.137.216 de WAN1. Solo queremos hacer que la IP externa 14.28.137.216 pueda acceder a este servidor. Nuestra topología está conectada de la siguiente manera.
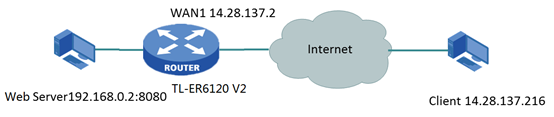
¿Cómo podemos lograrlo?
TL-ER6120 es un dispositivo NAT. El servidor web está en 192.168.0.2:8080 detrás de TL-ER6120. En primer lugar, abrimos el puerto de 8080 sobre 192.168.0.2 para todas las IP externas. Y luego configuramos el control de acceso para limitar solo la IP 14.28.137.216 para acceder al servidor web. Los pasos de configuración específicos son los siguientes.
Paso 1
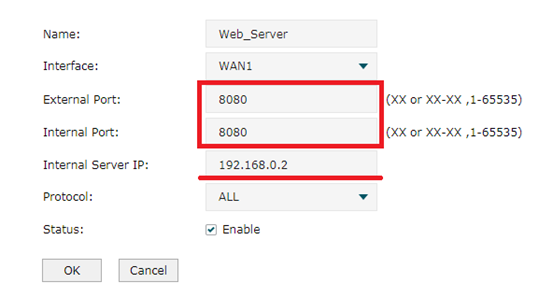
En este paso necesitamos abrir los puertos de 8080. Vaya a Advanced---->NAT----->Virtual Server. Para la interfaz, seleccionamos WAN1 y establecemos el puerto como 8080. La IP interna del servidor es 192.168.0.2. A continuación, haga clic en Aceptar. Cuando termine, se formará una entrada de regla en la Lista de servidores virtuales.
Paso 2
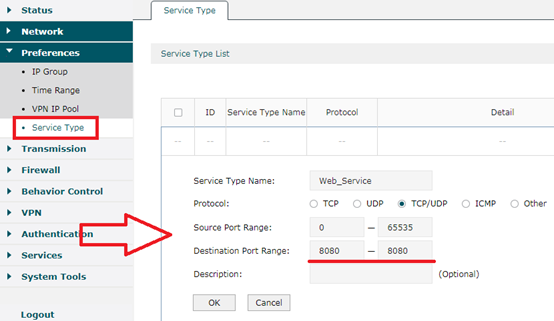
En este paso configuramos el tipo de servicio para que coincida con el puerto del servidor web 8080. Vaya a Preferencias---->Tipo de servicio. Asigne un nombre al tipo de servicio como Servicio web. y seleccione Protocolo TCP/UDP. El intervalo de puertos de origen es 0-65535. Rellene el puerto de destino como 8080. Haga clic en Aceptar.
Paso 3
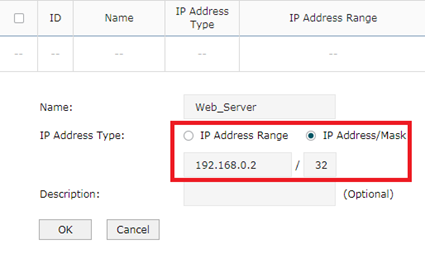
En este paso vamos a configurar el grupo de IP. Vaya a Preferencias----->Grupo IP---->dirección IP. Agregue la entrada como se indicó anteriormente.
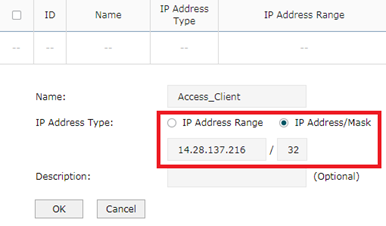
Access_Client mismo ocurre con Web_Server. A continuación, habrá dos nuevas entradas en la lista de direcciones IP.
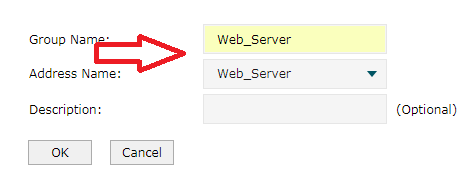
Vaya a Grupo IP. Corresponde al nombre de la dirección y al nombre del grupo. Ajuste de acuerdo con la imagen respectivamente.
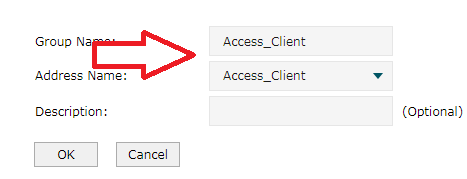
Este paso es sencillo. Empareja Access_Client con Access_Client Grupo entonces.
Paso 4 Configuremos ahora el control de acceso.
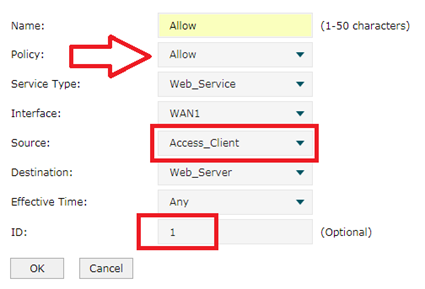
En el control ----> acceso al firewall, configúrelo como se muestra en la imagen de arriba. Primero seleccionamos Permitir política y elegimos Web_Service acabamos de configurar para el puerto 8080 para el tipo de servicio. En la opción Fuente, seleccionamos Grupo de IP, Access_Client establecimos antes. En destino elegimos Web_Server. ID como 1. A continuación, haga clic en Aceptar.
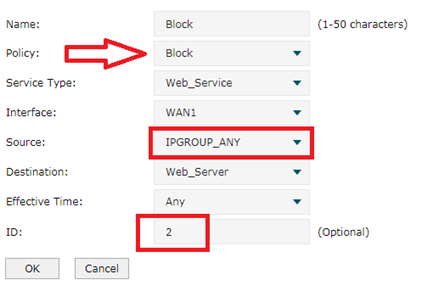
Y luego configuramos una política de bloqueo. La política es Bloquear y Origen es IPGROUP_ANY. No olvide establecer el ID como 2. Haga clic en Aceptar.
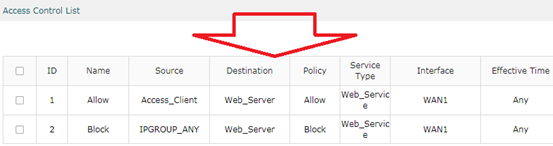
Después de terminar, habrá dos entradas en la Lista de reglas.
Verificación
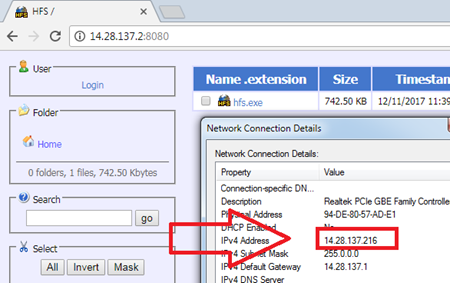
Como se muestra en la captura de pantalla anterior, en el cliente 14.28.137.216 escribimos 14.28.137.2:8080. (14.28.137.2 es la dirección WAN1) Encontraremos que puede acceder al servidor web normalmente.
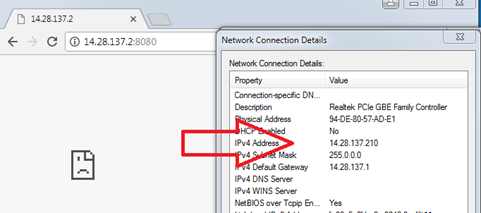
Y en cualquier otro cliente como 14.28.137.210, no podemos acceder al servidor web. ¡Funciona como se espera!
Nota:
1. El orden de ID de la lista de control de acceso presenta la prioridad y es importante.
2. TL-R600VPN podría satisfacer las demandas solo con la versión de hardware v4.
3. Para las diferentes versiones de hardware de otros modelos, habrá una interfaz de usuario diferente. Básicamente, el proceso de configuración de diferentes interfaces de usuario es el mismo que el de la interfaz de usuario del ejemplo. Falta de configuración de grupo IP, otras opciones de configuración simplemente cambiaron de posición.
¿Es útil este artículo?
Tus comentarios nos ayudan a mejorar esta web.






